脆弱性診断のベストプラクティス
無料キャンペーン実施中!
ホームページの脆弱性診断を実施する目的は何でしょうか?
現在、日本に対する不正な通信は年間5705億件を超えています。
不正な通信、サイバー攻撃から自社のホームページを守りましょう。
無料サイト診断実施中
このようなお悩みありませんか?
診断に時間がかかるので、
業務に負担がかかってします。
診断価格が高すぎて、
導入に踏み切れない。
診断後の開発相談ができない。
修正や開発は範囲外
と言われて困っている。
低予算・短納期 あなたの会社の経営をサポートします

安心の価格設定
他社を圧倒す短納期

信頼のアフターケア

脆弱性診断はリスクの早期発見と対応の迅速さが重要です。
脆弱性診断は、問題を特定し早期に修正することを可能にします。定期的な診断を行うことで、問題が発生した場合には素早く対応し、インシデントの拡大を防ぐことができます。
ウェブサイトの脆弱性が悪意のあるハッカーに悪用される可能性が高い現状があります。これにより、顧客データの漏洩、金銭的損失、評判の悪影響など、潜在的なリスクがあることを理解することが大切です。
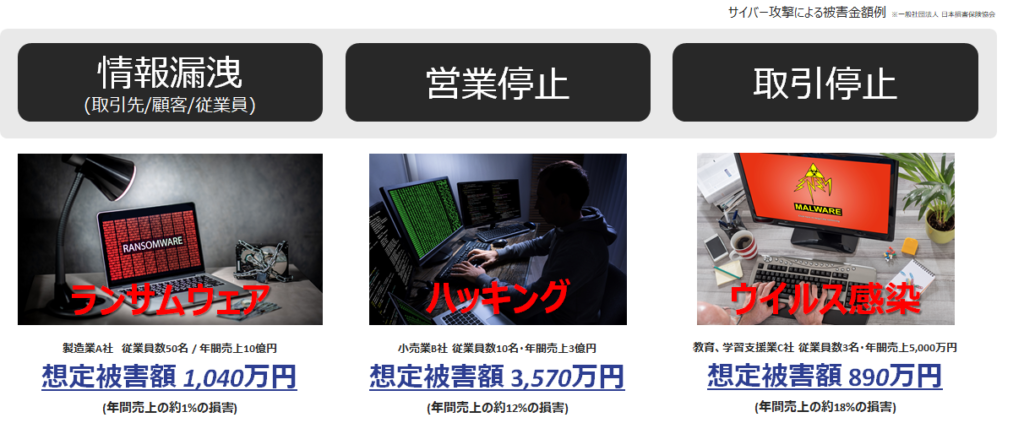
ウェブサイトの脆弱性による攻撃やデータ漏洩は、企業の経済的なインパクトをもたらす可能性があります。
脆弱性診断は、問題を特定し早期に修正することを可能にします。定期的な診断を行うことで、問題が発生した場合には素早く対応し、インシデントの拡大を防ぐことができます。予防策としての脆弱性診断の費用は、潜在的な損失や復旧コストと比較して非常に効果的です。
ウェブサイトの脆弱性による攻撃やデータ漏洩は、企業の経済的なインパクトをもたらす可能性があります。脆弱性診断を通じてセキュリティ対策を適切に実施することで、損害を最小限に抑え、事業継続性を確保しましょう。


脆弱性診断は、現代のセキュリティにおける重要なベストプラクティスの1つです。
ウェブサイトは企業の顔であり、顧客との信頼関係を築く重要な要素です。脆弱性が見つかり、それが悪用された場合、企業の信頼性や信用が損なわれる可能性があります。
顧客の信頼を維持するためにも、定期的な脆弱性診断が必要です。
経営戦略の一部としてのセキュリティ。
セキュリティは現代のビジネスにおいて重要な要素であり、企業の長期的な成長と成功に欠かせないものです。ウェブサイトの脆弱性診断は、セキュリティ対策の一環として位置付けることができます。
セキュリティを経営戦略の一部として取り組むことで、競争力の向上や信頼性の確立につながります。

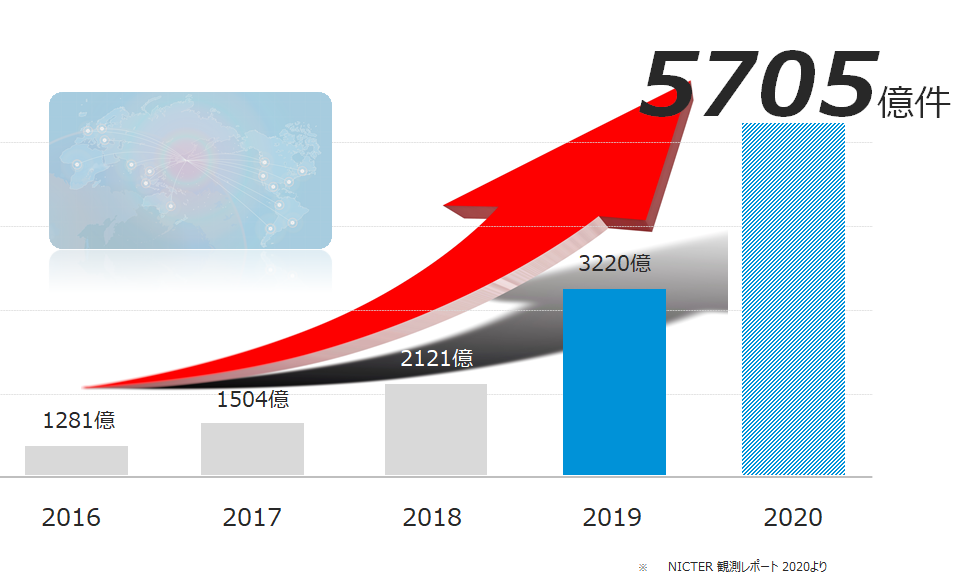
日本に対する不正な通信は5705億件にも上ります。
日本の法人数が 約180万社 ですので、1社あたり
約316,900件/年
となります。
1日(年間営業日数を245日とします)あたりで計算すると、1法人に対する不正通信は
約1,293件/日
となります。
不正通信が成功すると、サイバー事故(インシデント)が発生します。
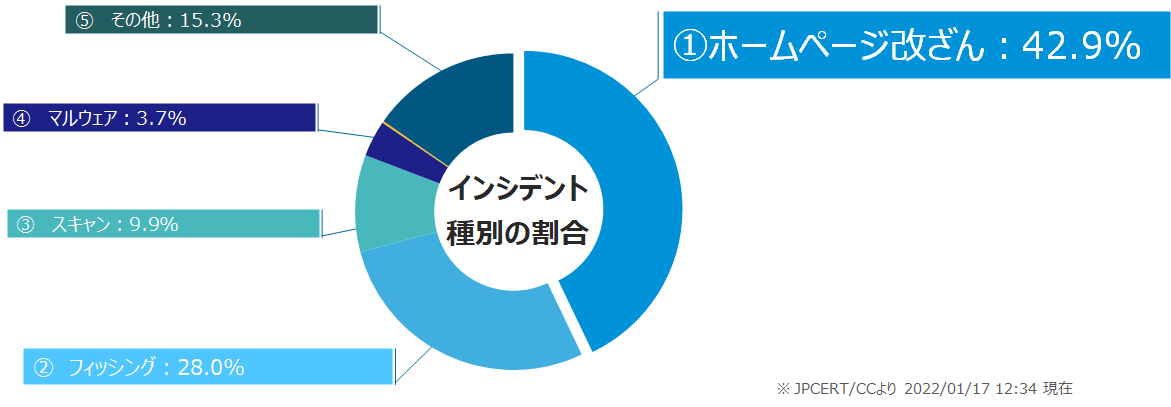
どんなサイバー事故(インシデント)が多いのか?はJPCERTでインシデント対応状況として公開されています。
こちらは、2022/01/17 12:34 現在のものですが、ウイルス感染よりもホームページに関係するサイバー事故(インシデント)が全体の7割以上となっており、ウイルス対策同様、ホームページにもセキュリティ対策を行う必要があることがわかります。
中小企業が狙われています。
中小企業の経営者にこそ、サイバー攻撃の対象とされてしまっています。
その理由は「踏み台」です。
大企業へウイルスを運ぶための踏み台として中小企業が狙われています。
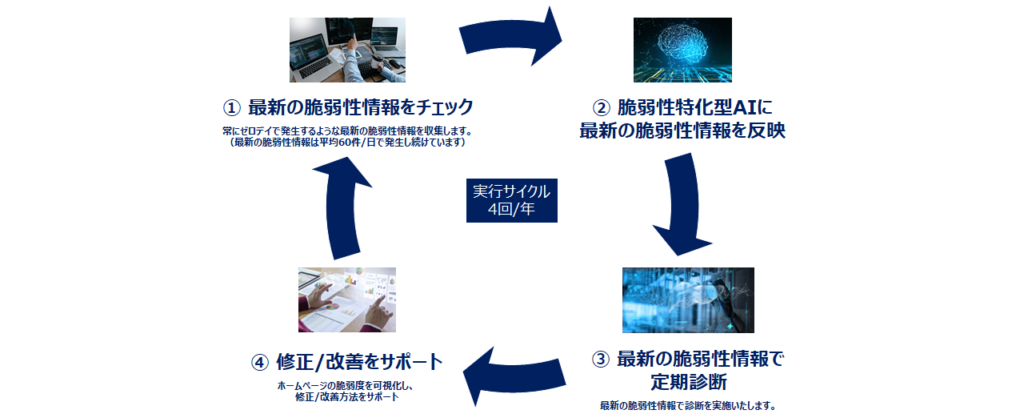
1. 定期診断サービス
年4回の定期診断で、最新の脆弱性をもれなくチェック。定期的に行うからセキュリティ対策は万全な状態に!

SANS Top 25 Full Coverage
OWASP Top 10 Full Coverage
PCI DSS 6.5.1-6.5.10 Full Coverage
AI Augments Human Testing and Analysis
Machine Learning Accelerates Testing
Authenticated Testing (MFA / SSO)
REST/SOAP API Testing
Business Logic Testing
Privacy Review Threat-Aware Risk Scoring
Step-by-Step Instructions to Reproduce
Web, PDF, JSON, XML and CSV Formats
Tailored Remediation Guidelines
PCI DSS and GDPR Compliances
CVE, CWE and CVSS Scores
OWASP ASVS Mapping
CWE-787 : Out-of-Bounds Write
CWE-79 : Improper Neutralization of Input During Web Page Generation
CWE-125 : Out-of-Bounds Read
CWE-20 : Improper Input Validation
CWE-78 : Improper Neutralization of Special Elements used in an OS Command
CWE-89 : Improper Neutralization of Special Elements used in an SQL Command
CWE-416 : Use After Free
CWE-22 : Improper Limitation of a Pathname to a Restricted Directory
CWE-352 : Cross-Site Request Forgery (CSRF)
CWE-434 : Unrestricted Upload of File with Dangerous Type
CWE-306 : Missing Authentication for Critical Function
CWE-190 : Integer Overflow or Wraparound
CWE-502 : Deserialization of Untrusted Data
CWE-287 : Improper Authentication
CWE-476 : NULL Pointer Dereference
CWE-798 : Use of Hard-coded Credentials
CWE-119 : Improper Restriction of Operations within the Bounds of a Memory Buffer
CWE-862 : Missing Authorization
CWE-276 : Incorrect Default Permissions
CWE-200 : Exposure of Sensitive Information to an Unauthorized Actor
CWE-522 : Insufficiently Protected Credentials
CWE-732 : Incorrect Permission Assignment for Critical Resource
CWE-611 : Improper Restriction of XML External Entity Reference
CWE-918 : Server-Side Request Forgery (SSRF)
CWE-77 : Improper Neutralization of Special Elements used in a Command
Injection Flaws
Many Other “High” Risk Vulnerabilities
Buffer Overflows
Cross-Site Scripting (XSS)
Insecure Cryptographic Storage
Improper Access Control
Insecure Communications
Cross-Site Request Forgery (CSRF)
Improper Error Handling
Broken Authentication and Session Management
A1 : Broken Access Control
A2 : Cryptographic Failures
A3 : Injection
A4 : Insecure Design
A5 : Security Misconfiguration
A6 : Vulnerable and Outdated Components
A7 : Identification and Authentication Failures
A8 : Software and Data Integrity Failures
A9 : Security Logging and Monitoring Failures
A10 : Server-Side Request Forgery
API1 : Broken Object Level Authorization
API2 : Broken User Authentication
API3 : Excessive Data Exposure
API4 : Lack of Resources & Rate Limiting
API5 : Broken Function Level Authorization
API6 : Mass Assignment
API7 : Security Misconfiguration
API8 : Injection
API9 : Improper Assets Management
API10 : Insufficient Logging & Monitoring
- サービスに関するお問い合わせ
- お見積り
- 脆弱性診断を取り扱いたいベンダー様
- その他ご相談
ご質問、ご相談等お気軽に下記よりお問い合わせください。